Steps In The Information Security Program Life Cycle Dod

Operation of the defense acquisition process.
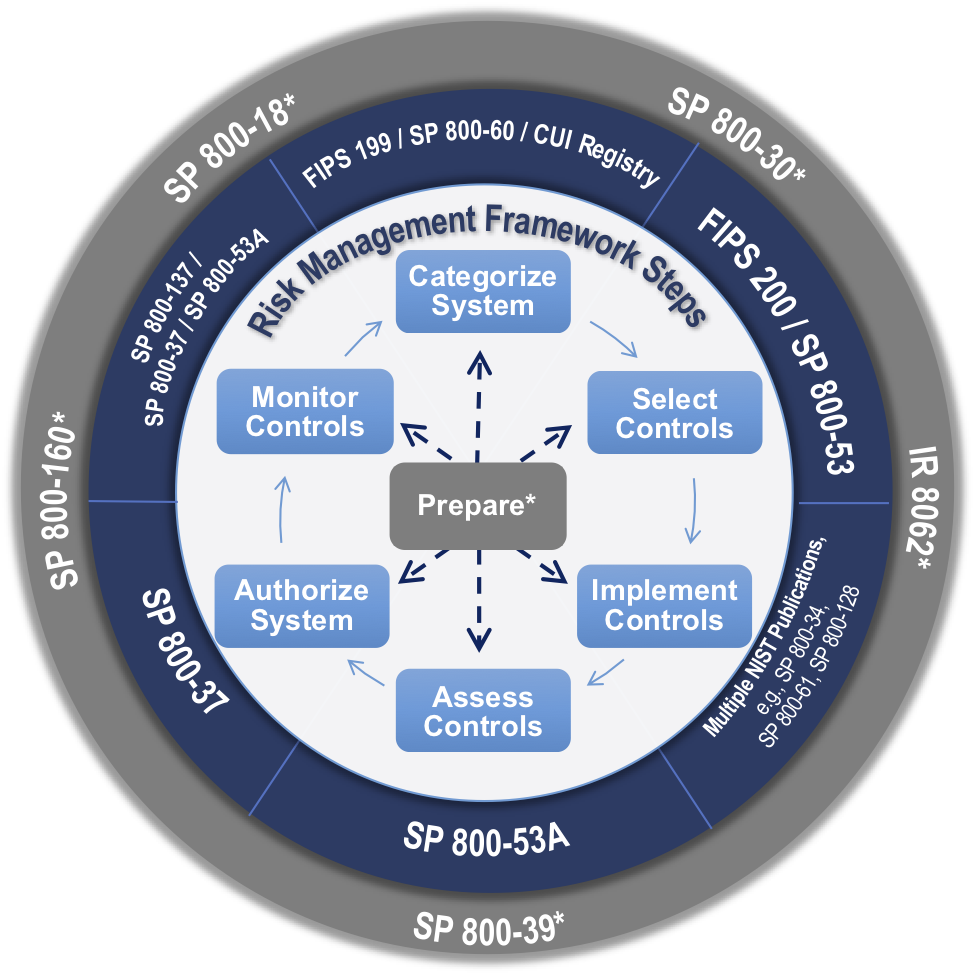
Steps in the information security program life cycle dod. And estimate potential. It also considers procedural physical and personnel security measures employed to enforce information security policy. Specified set of security requirements throughout the life cycle of the information system. Identify the feasibility of designing and developing defense exportability features def for the system.
During this course you will learn about the dod information security program. Usd i dodm 5200 08 vol 3. The six steps of the pdlc are analyse the problem design the program code the program test and debug the program formalize the solution and maintain the program. The modern day information security program has been evolving since.
A information security program is the set of controls that an organization must govern. Protection of classified information. What are the steps of the information security program life cycle. Dod information security program.
A security life cycle approach. Procedures for the dod personnel security program psp usd i dod 5200 08 r. Classification safeguarding dissemination declassification and destruction the unauthorized disclosure of confidential information could reasonably be expected to cause to our national security. Assigning a lower classification level to classified information because the information requires less protection in the interest of national security.
What is a repository of scientific and technical documents for the united states department of defense and serves the dod community as the. Life cycle management lcm life cycle management is the implementation management and oversight by the designated program manager pm of all activities associated with the acquisition development production fielding sustainment and disposal of a dod system across its life cycle jcids operation manual. It covers the information security program lifecycle which includes who what how when and. National industrial security program operating manual nispom dod 5220 22 m.
Program level exportability feasibility studies should be conducted as early as possible in a system s life cycle to assess the international market for potential cooperative programs foreign sales or transfers. It is important to understand that a security program has a continuous life cycle that should be constantly.