What Are The Steps Of The Information Security Program Lifecycle Stepp
During this course you will learn about the dod information security program.
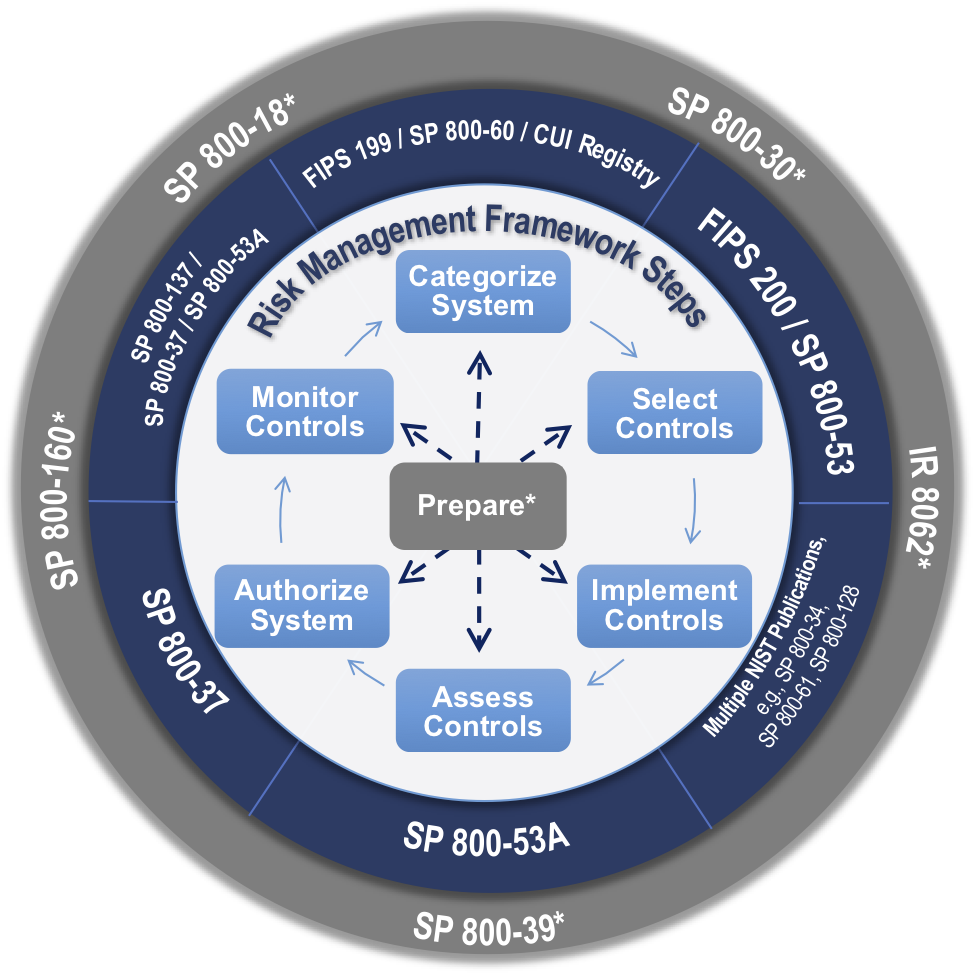
What are the steps of the information security program lifecycle stepp. Students will be provided with a basic understanding of the legal and regulatory basis for the program how the program is implemented throughout the dod and an introduction to the information security program lifecycle. It is important to understand that a security program has a continuous life cycle that should be constantly. Introduction to information security. The steps of the information security program lifecycle are.
Are the steps of the information security program lifecycle. It covers the information security program lifecycle which includes who what how when and. We agree with this statement but we also believe that these life. Expert answered taki points 396 log in for more information.
The six steps of the pdlc are analyse the problem design the program code the program test and debug the program formalize the solution and maintain the program. Classification safeguarding dissemination declassification and destruction. This course provides an introduction to the department of defense dod information security program. This course will provide a basic understanding of the program the legal and regulatory basis for the program and how the program is implemented throughout the dod.
A information security program is the set of controls that an organization must govern.


















